An interesting skill we have honed over the years has been the use of OSINT techniques to gather information on a client company. For those new to all this, it’s ok because you can follow quite easily and should learn a few things that might help with everyday life.
Let me apologise for the first obscure word used already ‘OSINT’ This stands for ‘Open Source INTelligence’ and a little like ‘Devops’ or ‘Cloud’ It’s massively overused, misunderstood and confused. Quite simply it’s information about something that isn’t restricted behind secure access, but open. Sometimes it’s not easily open but it’s there, in all the obscure corners of the internet.
The other thing to note is we do all this to give companies perspective and help.
Email Addresses
Love it or hate it they aren’t going anywhere fast. With so many attack vectors reliant on a strong initial phishing campaign the hunt for email addresses is never ending to any social engineer. Email addresses are used as usernames, they can be googled and this can connect the fragments of our online life together. To hunt these email addresses, attackers use specialised tools but you can see the power of some of the tools below with an example using Apple’s Automator program and The Harvester. Often simple google searches can return hundreds of thousands of email addresses as shown here.
Every company will have a few visible email addresses but awareness must be drawn to staff emails that appear using popular online tools, these email addresses are at high risk and should be subjected to more stringent checks.
Social Media
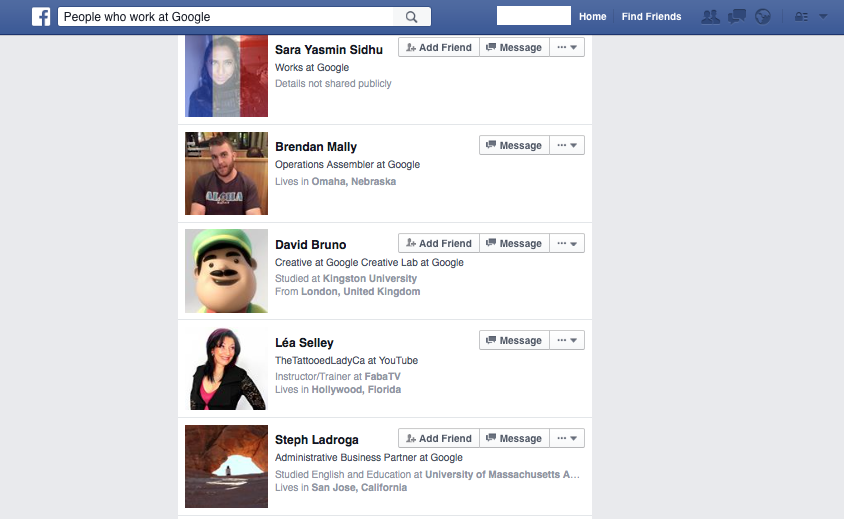
We are mostly all aware now that if we update our job role on LinkedIn other people can see it. These minor information leaks often will get disregarded and I answer questions such as “Why does that even matter?” it’s actually a very good question! For most people it’s really hard to gain the perspective of an attacker. It’s all so far fetched and people disregard the threat that exists. What I guess I am suggesting is thousands of people around the world have a malicious financial interest in you and constantly look at you directly and your place of work looking to exploit it… It sounds like the ramblings of a mad man yet the statistics are there to support this wild theory and the numbers of victims constantly rise.
Abusing the way social media platforms share our information we can discover very relevant details. Some simple yet effective techniques don’t come from high tech tools but from the sites themselves.
When an attacker is targeting a company there is a need to focus this attack on people within an organisation that have power and access to the resources of the company. The difference between “Works at Google” and “Works at Google, Payroll Services” could mean you become a focus in this inbox onslaught or don’t.
Staff Phone Numbers
A common theme amongst scammers is they nearly always abuse our helpfulness. In the first section I showed how you can obtain large lists of email addresses in minutes, next we will try to get even more information from these email lists. Lets start by sending 1000 people a blank email (we’ve now crossed the OSINT line like any attacker will). No effort required, just BCC them all in and click send. Wait 10 Minutes and your inbox will be littered with out of office details that give up more information than expected. I guess if you were the good kind you’d just take note of these details and Cassandra’s maternity leave but if you were not it’s trivial to scrape thousands of email addresses for contact numbers in the out of office reply alone.
Sorry I am on scheduled leave, please take this phone number I wouldn’t normally give out and if you want to target other workers there is also a colleague I have CC’d In along with my role and full name on the signature for you to stalk me online, thanks.
Profiting
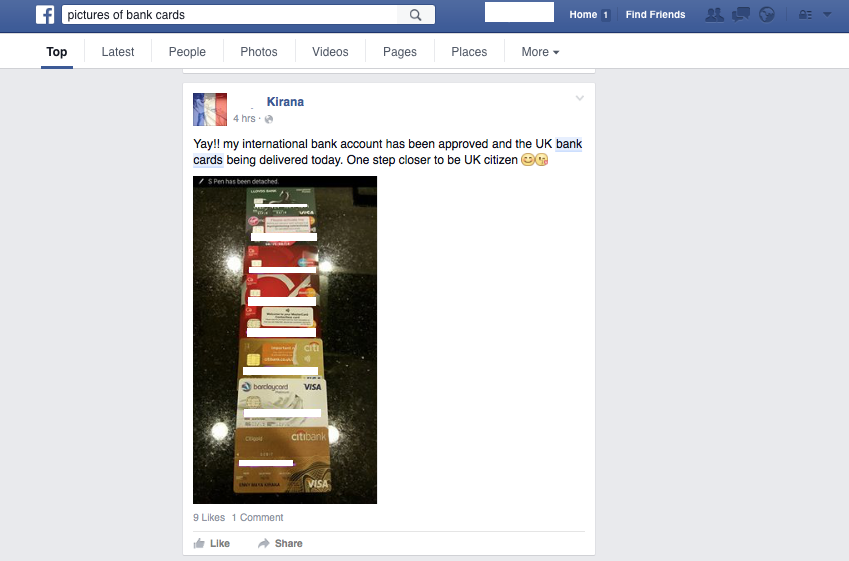
So, the information above doesn’t even begin to detail the technical capabilities of the bad guys. It’s just to display one tiny little trick in a toolbox of other tricks. These are used to hunt for victims online, they spot bank details and card data. These skills are an integral part of nearly all online financial crimes and you should be aware of the stuff you share to help combat these kind of attacks.
Advice
- Google your own name and address and get to grips with information you discover.
- Google your own email address and setup Pastebin and Google alerts for a mention of it online.
- Obtain a free credit report and be on the lookout for signs you’ve become a victim.
- Only use credit card details at reputable places, never a new online shop.
 Richard De Vere (@AntiSocial_Eng) is the Principal Consultant for The AntiSocial Engineer, he has an extensive background in penetration testing and social engineering assessments, including ‘red team’ exercises and information gathering assessments for financial institutions and some of the UK’s largest companies.
Richard De Vere (@AntiSocial_Eng) is the Principal Consultant for The AntiSocial Engineer, he has an extensive background in penetration testing and social engineering assessments, including ‘red team’ exercises and information gathering assessments for financial institutions and some of the UK’s largest companies.