For many victims of SIM Swap Fraud, the first time they learn about the attack is in the hours after their life has been changed forever.
It’s an all too common story, the signal bars disappear from your mobile phone, you ring the phone number – it rings, but it’s not your phone ringing. Chaos ensues. You’re now getting password reset emails from Facebook and Google. You try to login to your bank but your password fails. Soon enough the emails stop coming as attackers reset your account passwords. You have just become the newest victim of SIM Swap Fraud and your phone number is now at the control of an unknown person.
Hours, sometimes sleepless days later you get to piece it all together. Your bank account is empty, your emails and data have been downloaded and deleted. Your credit file is in pieces and all you have is a ransom demand for cryptocurrency from the hackers to show for the ordeal.
The AntiSocial Engineer published our rather damning original study on Sim Swap Fraud in May 2016, take a look here.
Since the previous article, we have been contacted by victims affected by these attacks on an almost monthly basis. Their first-hand accounts of what has happened are haunting. They write in so naive to the whole event and we feel so hopeless reading their accounts, retrospectively little can be done. We provide victims with free help and advice where possible but it doesn’t ever feel enough.
Recently one message got to us though, it wasn’t the usual. Especially in our vocation, we can forget why it is we wake up in the morning and do what we do.
“I just want to know what these ‘hackers’ know about me, help me.”
The statement isn’t someone chasing their money back, it’s obviously one derived from fear. We decided to look at this case and review Sim Swap Fraud once more. What we found was saddening, so much so we thought it was time to blow the lid off this mess and make some of our companies behind the scenes work a little less secretive. Buckle in.
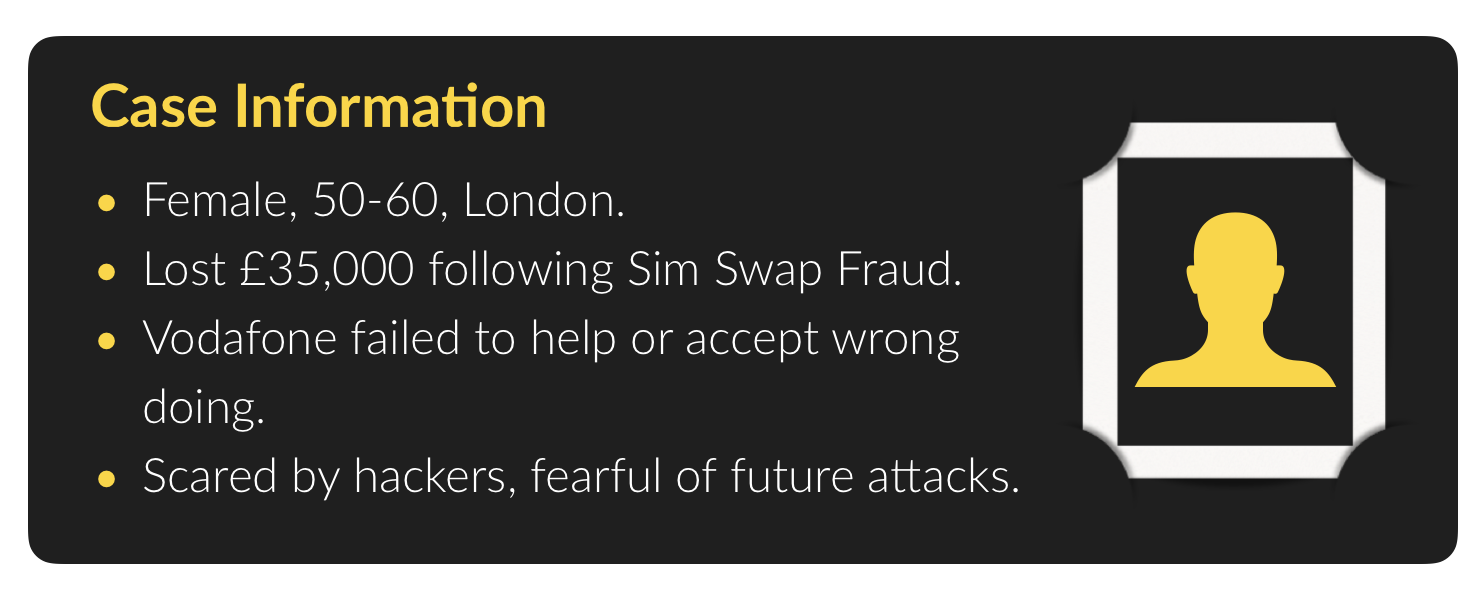
A fraudster rang Vodafone prior to the actual SIM Porting process. They successfully obtained the victims Porting Authorization Code (PAC) that was later used to gain access to her online accounts and bank account. Simply by changing the SIM card her number was registered too. A payment for £35,000 was successfully sent to a bank account in Slovakia and was ‘clearing’. Online social media accounts were targeted after financial accounts.
Our victim contacted Vodafone and was less than happy about the scenario, Vodafone did little to help nor did they take steps to prove the request was legitimate. They even charged her £29 to port her stolen number back to the account. They did not inform her of the call made by the attacker at all. Vodafone did nothing significant to inform her of what had gone on. After reading our previous blog she reached out to us and wanted to know what ‘they’ knew about her online life. She felt violated.
We arranged to speak later that day and we dealt with her case pro-bono.
Seeking the truth, practical tips to prompt Vodafone into admitting what had gone on were issued. Later that week we got a reply, one of the best emails we had ever received, it was from our victim. Vodafone had been forced to acknowledge what had happened to our victim, assuming liability.
We cite our victims account of this inbound vishing call to Vodafone, it was only short but the malicious Social Engineer was able to get what they wanted. After help from The AntiSocial Engineer she was able to get straight answers and a transcript of the call from Vodafone:
- A person called Vodafone asking to change victims PAC.
- They were calling on behalf of ‘the victim’ as they apparently didn’t have a mobile connection.
- This individual didn’t know;
- Any of the account passwords or memorial words.
- Any contacts on the phone
- How much the monthly Direct Debit was for the account.
- Victim’s date of birth
We were able to use OSINT (Open Source INTelligence) techniques to find a financial motive for a fraudster to target our contact. Public Facebook privacy settings allow for a glimpse of our victim’s lifestyle – not exactly dressed in furs and dining at the Ritz, but ‘comfortable’ would be a polite statement.
We looked at the ways used by the fraudster to link her mobile phone account to her online persona. Then later we focused on the inbound vishing call made by the fraudster and the way in which Vodafone didn’t seem to take steps to validate the caller’s details at all.
Is Vodafone to blame?
We think so Yes. In our previous work on SIM Swap Fraud in 2016, we recorded a call to Vodafone where we detailed just how easy it was to steal a phone number from one of Vodafone’s account holders using a vishing call. The poor, overworked call centre worker didn’t really seem to care and actioned the request without checking it was legitimate.
The vishing calls we made to Vodafone in 2016 accompanied an article that was later picked up by Vice media. It also struck a chord with a few government types and we made some amazing connections.
But in 2017 it got stranger, in the course of our day to day testing activities with a client we came across a way so deviously effective at stealing a UK phone number we knew we couldn’t blog about it before it came public knowledge, we googled and it was nowhere to be seen online. Our simple technique combined with an easy vishing call meant we could steal almost any mobile phone number in the UK. We didn’t know what to do with this information.
Luckily, we were not the only ones interested in our new found talents. Around August 2017 we agreed to have a meeting in London with the Metropolitan Police, NCA, FFA UK, NFIB and the NCSC and shared the precise details of our ‘new’ attack vector. Unknown by us, our extra bit of information was somewhat the ‘missing piece’ of the puzzle they were unable to solve. Behind the scenes, the police were dealing with a wave of SIM Swap Frauds and it was becoming an issue but they couldn’t understand how attackers were gaining the ICCID (SIM Number) and using it to validate porting of victims phone accounts. We even got a little plaque for helping them, which I assume is their way of saying thank you.

A plaque from the MET to say thanks.
We kind of naively thought that would be the end of the matter, the ‘higher-ups’ would fix everything and mobile phone users would live forever in harmony… but since then, a year later we find the same exploit being used by fraudsters.
Vodafone would like to have us believe this is an isolated event. But it is not. They have a serious issue with delivering PAC codes, just look on social media to find numerous cases of victims left in the dark and shouting about their horrific ordeals. Vodafone has not implemented the free advice we provided to them in 2016. When any fraudster rings up they provide you with the PAC code over the phone. They seem unconcerned by this problem. In their press statement supplied for this article they state;
“Vodafone has robust controls in place to protect our customers’ accounts against fraudulent activity. We routinely monitor their effectiveness and adapt security processes and staff training as new fraud issues emerge.
Our previous response in 2016 was specific to the case highlighted at that time. In 2016 we provided customers with their PAC code over the phone as well as via SMS once sufficient security checks had been successfully completed and that remains true today.
Vodafone does not use the number on the back of SIM cards (described as the ICCID) as proof of SIM ownership, but check this data in combination with a broader set of security checks that have proven to be effective in combatting SIM swap fraud.” – Vodafone UK
The most basic of precautions have been ignored by Vodafone, ones happily adopted by EE following our 2016 blog and supported by O2 – that have had secure processes in place years earlier, and continue to balance the needs for security and customer experience. Vodafone state they don’t use the ICCID as ‘sim ownership’, but do still use it with “a broader set of security checks” whatever that means… In fact, the ICCID has been used to expedite fraud on several thousands of cases.
So that clears up our concerns really, case closed, they admit to issuing the PAC code over the phone and their agents can still be tricked easily. We even emailed them back after that press statement to see if they wanted to include ways they could help their customers, our reply:
‘We would like to publish a more thoughtful answer, one that attempts to address the problem you have internally with validating SIM Swaps and begins to rectify the issues you have to better secure your customers.” – @AntiSocial_Eng
They confirmed they did not want to do that and their original statement stood.
So what now?
Our concerns have been reported to the ICO (21:01 pm 23rd July 2018), this is mainly due to the widespread problems with how Vodafone handle customer data in general. SIM Swap Fraud is happening at such a rate we should start thinking of this as a significant amount of customer data ending up in the wrong hands and not as ‘isolated incidents’ that are unrelated to each other.
We urge Vodafone once more, please make changes – Make it impossible for the call agent to see the PAC in a call. Use an automated system that sends it the device only via SMS!
Whilst the broader issue is at the control of Vodafone and other telecoms operators to rectify, we feel we can help victims deal with this in a more efficient and fairer manner.
So let us recap on what we suggest you do if you are the victim of a SIM Swap Fraud Attack. Here is our 3 step plan in dealing with your operator.
Victims Guide To Dealing With Your Carrier
- Know what they know. There is no incentive for a company to help you in this scenario as cases can be damaging to them. They will not advise you that you have been the victim of their incompetence. We need to use a few of our rights to receive the data and make our own conclusions. Often, they will come clean at this point like they did with our victim. We have been lucky enough to receive a template Subject Access Request (S.A.R) letter from an expert on the matter. Rowenna Fielding is a highly experienced privacy and information security professional working for Protecture, a firm that provides data protection advice and support. She kindly provided us with a PDF template. Fill in the details on this PDF and send this request to your operator.
- Get your money back. Banks will normally be a little cautious. Whilst some do offer SIM swap fraud victims a refund, many don’t. In the banking terms and conditions, you are responsible for your passwords and some means of authentication. You could find yourself in a tricky spot trying to explain this was not your negligence at all and in fact it was that of a third party. Having the proof from your S.A.R request should help clear this up.
- Stop it happening again. Vodafone, for instance, has a feature where all account changes have to be done in person in a store – all you have to do is ask for it. Still not foolproof but a massive step forward. Other operators have similar ways in which you can apply extra security and notes to the account.
Need a Lawyer?
If you have been the victim of “Sim Swap” and would like to discuss your entitlement to compensation with a lawyer, we can help.
We have partnered with a leading firm of data rights lawyers, JMW Solicitors LLP. JMW represent SIM Swap victims, including on a “no win, no fee” basis.
If you would like to speak to JMW, please email [email protected] with your query and JMW will get in touch with you asap. Please don’t forget to mention that you read our blog!


