From the very start of being interested in ‘hacking’ and Information Security I do wonder what influences the style, the culture… I mean we all love InfoSec redteams and the ways for a brief moment our minds provide us with superpowers. But why the hoodies, balaclavas, L337 D@nK0ver|0RDp usernames? I don’t get it, we have special abilities, we can traverse barriers, discover magic and peer down on the muggles… but is there another, more professional way? Is our echo chamber limiting our understanding of modern IT challenges?
I apologise for the cryptic intro but I wanted to paint a clear comparison. For too long it’s been an ‘us vs them’ issue. I often think it’s the blue team that can learn from our ego fuelled experiences… but we think redteams could learn a thing or two about attacking from many blue teams too!
Blue-team tools in my toolbox
This is not another guide about some essential blue team tools you must have this season either, it’s hopefully not vendor hype and certainly isn’t sponsored! It’s our take on doing what social engineers do best – thinking outside the box!
What if… the best kept secret red team tools were actually blue team tools! What if we were doing it wrong?
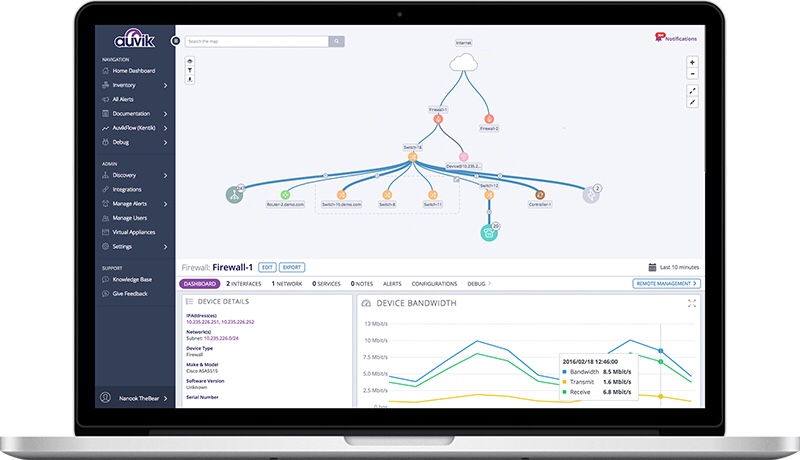
NMAP vs Auvik
Everyone should learn to use NMAP. But when looking for comparisons and alternatives to this tool we fall in the habit of looking to other CLI based networking tools. When we design a Dropbox for an engagement we install NMAP and it’s one of the first tools that will help explain our new home on the LAN – usually in a meeting room under a table! But let’s compare this to Auvik…
You install an Auvik agent on a device, plug it in and within minutes you’ll have a fully interactive network topology diagram. It scours ICMP and SNMP on your network to build this beautifully efficient picture of what’s available. No ones looking for it, let’s be straight if they haven’t got NAC and you’ve plugged in a box – they are unlikely to have IDS… with a little social engineering it will just blend right in to your network… sit back and access the portal from anywhere in the world and view everything you couldn’t see clearly with NMAP. Auvik has everything mapped and ready for attack.
AutoSSH vs OpenVPN
On our older Dropbox designs we relied on a 3G dongle, AutoSSH with a Raspberry Pi. Reliable, but inferior to OpenVPN. We’ve learnt the hard way, corporate grade tech is better. Static Cellular IPs, Industrial MDM connections, OpenVPN on an adults micro-computer. It’s not in the hacking spirit but it removes the headaches and issues – you shouldn’t be worrying about your SIM card running out of credit whilst you are exfiltrating data (yes, mid assessment we shifted so much data we had to top up again). I don’t want to proxy ports over SSH! I want my work devices on your network!
OpenVPN offers a stable connection and does the job a lot cleaner. Accessing a dropbox via OpenVPN from an iPhone in a restaurant with your family – priceless.
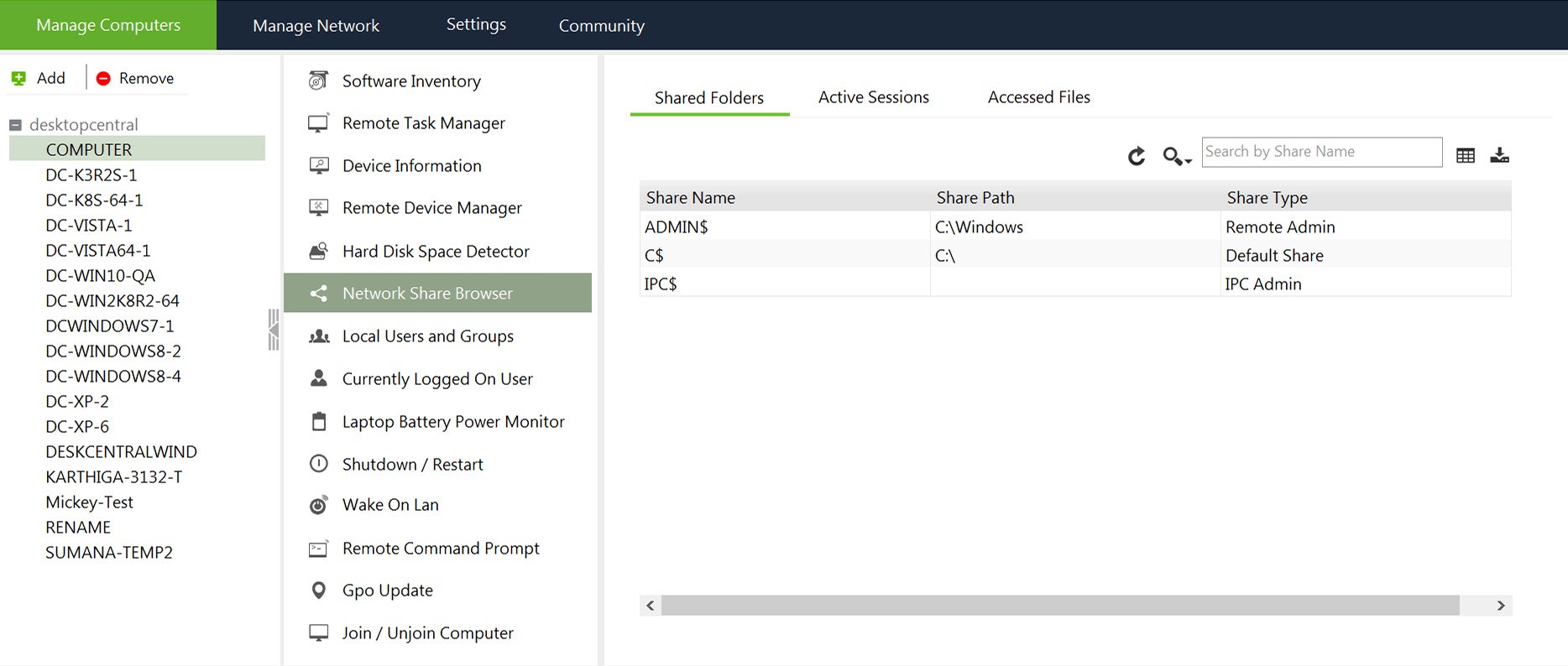
Hunting For network shared drives CLI vs Network Share Browser
For me, Linux is home. But it’s not the fastest way to start rifling through your clients network shares. Network Share Browser from ManageEngine was just one of about 3000 tools that mostly do the same thing. I found it useful to use and collate information that would be used in later attacks. It works and looks nice.
Chuck Kali Away?
Of course blue team tools lack the focus on the attacks, but they can bring valuable insights to a penetration test. Even the humble NMAP can be a great attack tool,so we’ve understood the potential even basic programs designed for network maintenance can have.
I’m not saying ditch Kali Linux for Windows Server any time soon, but keep an eye on what they are using over in corporate world – drop the attitude of smashing companies and chucking them vulnerability reports and start to talk.




















