Normally we take pride in demonstrating a cutting edge social engineering technique, but as I write this article the only feeling I have is utter dismay. I am ashamed of the regulatory body.
Ofcom (The Office of Communications, the UK government-approved regulatory and competition authority for the broadcasting, telecommunications and postal industries of the United Kingdom) recently boasted about their new SIM Porting procedure. They publicise the fact UK mobile customers can now port their phone number to another network even easier than before – with a simple SMS message. In doing so they may have just opened up the biggest risk to innocent consumers we have ever experienced. But is it all bad?
MNP
Seen as something of a right, consumers have the ability to port (transfer) their phone numbers to another mobile network. The MNP Process (Mobile Number Portability Process) has been the subject of numerous blogs on this site and in 2019 we expected any big news on the subject to be positively addressing the spate of SIM Swap Frauds encountered by victims. Whilst MNP is a potentially good thing for preventing customers from being locked into an unhappy arrangement with their operator, companies have failed to address security concerns surrounding the process.
The new way to port your number
From the 1st of July 2019, UK mobile users will be able to port their number with a text message sent to 65075. You simply send PAC to 65075 and within a minute, a message will be returned to the device.
Whilst their own video demonstrates the process including basic security checks (asking for DOB) we have discovered that in reality, this is not the case with several UK networks. Ofcom has failed us and they have failed us hard.
Can’t hack? Just ask Siri
So why has this hobbyist author been so down in the dumps about the latest changes?! Well, it’s because Ofcom has failed to listen. Year on year practical exploitation of security issues has become easier. The new SIM Swap process could be conducted by a 5-year-old. If you doubt this claim I have prepared a demonstration. Not heard in the video but Siri is reading out the PAC code seconds after the request.
What Now
By shifting the attack vector, SIM Swap Fraud has now become a serious concern for anyone utilising Siri. In fact anyone with temporary access to your mobile phone can exploit this issue. It takes just 30 seconds with the targets mobile phone to obtain the PAC code and can provide access for up to 30 days after. Sure, we can disable Siri, but the attack is still possible via other methods.
I do believe Ofcom had good intentions, but the new changes have obviously not been double checked by anyone with experience in this field. They probably thought the issue was solved as the scammer would need the phone to be physically in their possession. In reality what they have done is lubricated the whole SIM Swap process and actually made it easier to exploit – both locally and remotely. We were so concerned that national security was left to ‘an incidental lack of foresight’ that we requested further information from Ofcom using a freedom of information request.
As mentioned, It’s not even limited to Siri users, any unsuspecting victim could be stung with this new method using fairly basic social engineering techniques.
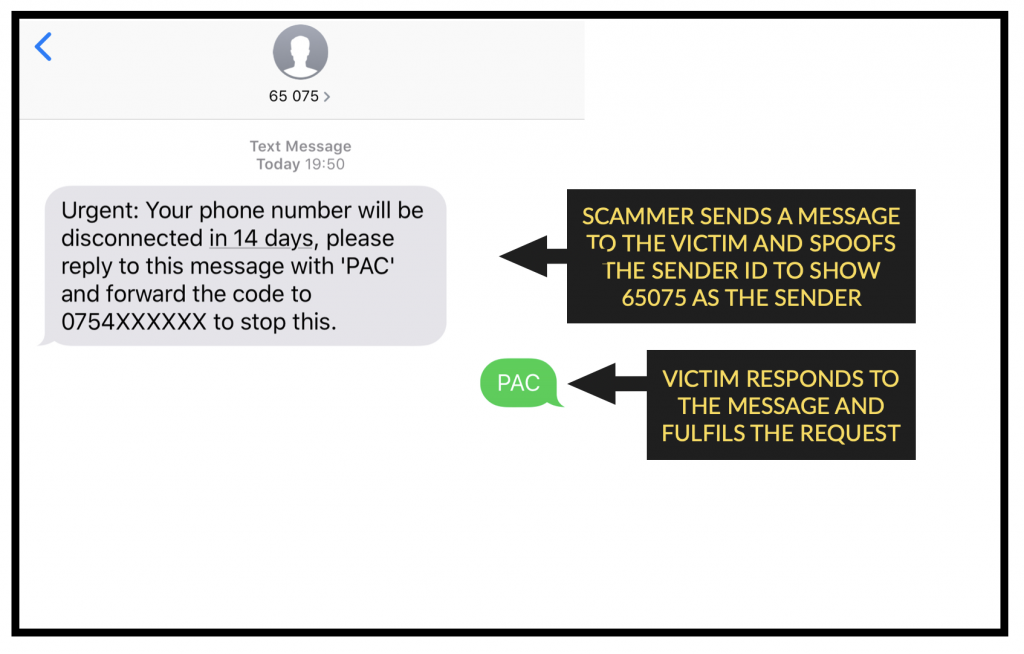
- You receive a spoofed message from 65075
- You believe the social engineer’s lies.
- You send your PAC code off to ‘stop your number being disconnected’
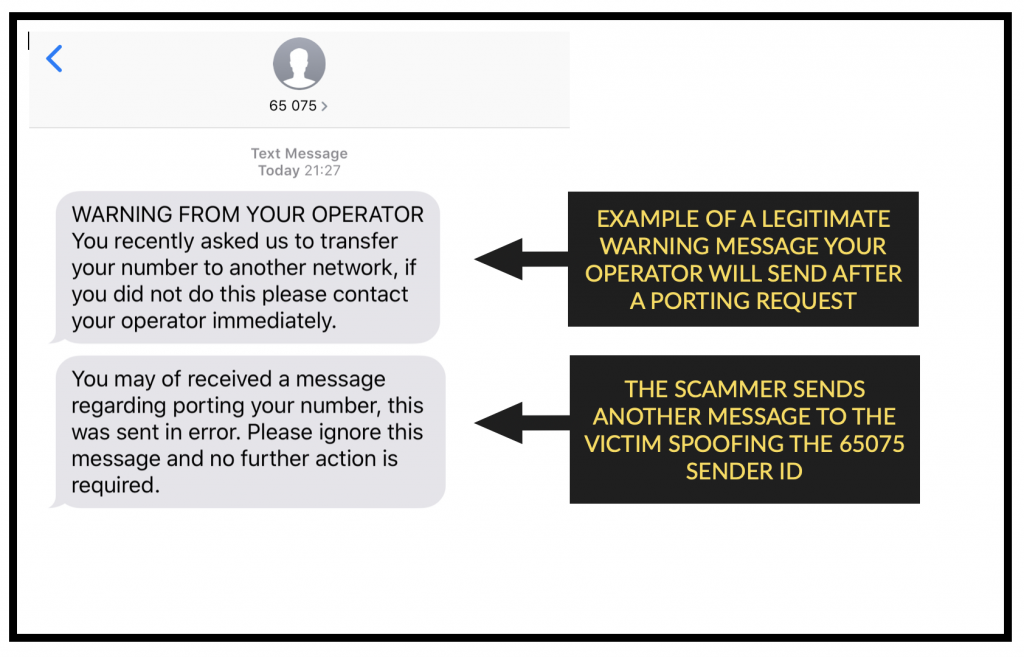
- The criminal ports your number and sends more spoofed messages claiming the warnings you got from your operator are a mistake.
Immediate Safety
I sincerely hope the following tips help.
- Do not provide access to your mobile phone to anyone.
- Disable Siri
- Be aware it is not just Siri that allows this – access to your SIM card can also be exploited by the use of a secondary phone.
- Understand that SMS messages are inherently insecure, the sender’s number or name can be spoofed.
- Spoofed messages are automatically displayed in the same SMS conversation on all modern phones.
- Be on the lookout for sustained loss of signal or ‘No Network’ displayed on your phone – contact the carrier immediately
- Seek help should you receive ANY message mentioning leaving the network
- Start to discontinue use of SMS authentication services, exchanging them for mobile based applications like Google Authenticator.
Ofcom
I have decided not to contact Ofcom for a statement. They didn’t listen over the past few years and I am sure they will only offer a PR focussed spin on things. Why should we live in fear of this happening when innocent customers have had no part in this decision and Government organisations have failed us. The injustice hurts so much. It’s another case of organisations too big to listen, doing what they please.
The new changes are simply shifting liability away from carriers on to the shoulders of innocent people. It’s in support of operators and does not reflect the intended nature of the Ofcom… which in quoting their own website’s about us page:
“We also help to make sure people don’t get scammed and are protected from bad practices. This is particularly important for vulnerable or older people.”
Ofcom’s About Us Page
RECEIVE OUR NEWSLETTERS
BLOGS • SECURITY NEWS • EVENT INVITES • COMPANY NEWS • TIPS AND ADVICE


