For those of you wanting a technical debrief of what happened, this blog might not be for you. I actually want to focus on something completely different. Please take the TL;Dr and be on your merry way. This is a blog about a day off, food with family and how this led to one hell of a bug bounty and some personal learning points.
TL;DR – A logic flaw on the WeChat account signup process was exploited by a spoofed SMS, this led to a no interaction account take over scenario. A directly related issue also meant we could create a new account registered to a phone that doesn’t exist such as +44700000000. We reported this directly to Tencent as per the terms of TSRC bounty program.
Pushing the boat out’!
The rural settings of the Yorkshire Pennines is a nice place to live if you just tweak a few things. One of the essential adaptations is to the culture. Yes, Yorkshire has a rich heritage and I’ve had fun learning about the history, the growth of the coal industry in the industrial revolution and I grew up in a real life Lowry painting but after a long week at work give me colour, cocktails, Mexicans, Chinese food and some pizazz.
We met up at a Thai street food restaurant with friends and attempted to ‘push out some kind of boat’.
During the meal I notice everyone paying with WeChat, it was seamless. A few words of Thai and a wave of a phone. It sure would be cool to see what all the hype about WeChat was I thought.
There with one smartphone, one Monzo card and one bill that needed paying, I dive in and install the app.
Am I the one being Setup?
So relatively engaged in conversation, the signup is simple and easy and requires zero attention. It’s tied to a phone number cool, thats easy. I tap away then it asks me to send a text message to a number to confirm my ownership of that number. The whole account creation and single instance sign in process reminds me of WhatsApp.
At this point I was just chuffed it all kind of worked. But one thing from the account signup process struck me and was replaying over and over. You sent a text message to them, this could be spoofed. You could spoof the number Rich.
On a personal level with you all, I work too much, I find it hard to switch off and at this point of scheduled entertainment time I really didn’t want to go grab a laptop and ditch everyone. I settle for a quick logic check:
They have a billion users and I ponder the chances that an obviously exploitable issue such as SMS spoofing is left right there for me to find in the middle of food. I tell myself to switch off and pay with the Monzo because it all freaked me out. Setting up a new payment source was never going to be the cool talking point for the meal I secretly hoped it might be.
Switching Off!
Didn’t happen. I asked my partner to drive home from the meal and cracked a laptop out on the way home… minutes later, I had finalised the WeChat account creation, but by sending a spoofed SMS message using my mobile number as the sender ID. This tricked the WeChat authentication system and effectively created my own account but without my mobile phone sending the message. A nice party trick that I ponder.
Later that day I ask someone to create an account genuinely on their own phone and I test various things such as hijacking the number. I try the lost password feature and it offers to send a text message to the device which is useless to me and would alert someone too!
So I tried to create a new account with that number to see what would happen in that scenario. The signup process asked me to send an SMS to their mobile endpoint but I was expecting something to stop this process somewhere.
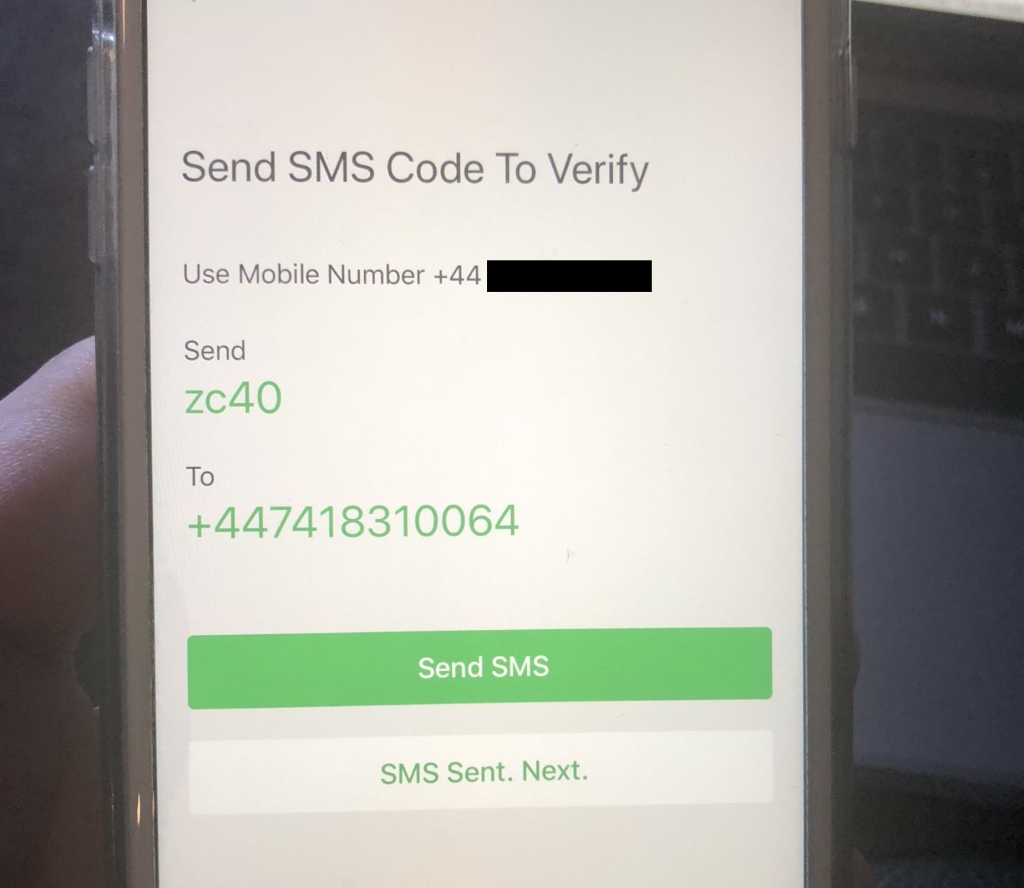
After sending the spoofed authentication message, tapping on ‘SMS Sent. Next’ informed me that an account with this number already exists. But it gave me the option to take ownership of it and set a new password which was great. It was now possible to steal accounts but I was sure there was something I was missing. The whole event seemed too easy. Left with more questions than answers. Maybe WeChat used the IP? It’s a similar phone? is this some intended feature? Maybe because we have Apple Family enabled? Maybe it is something else…
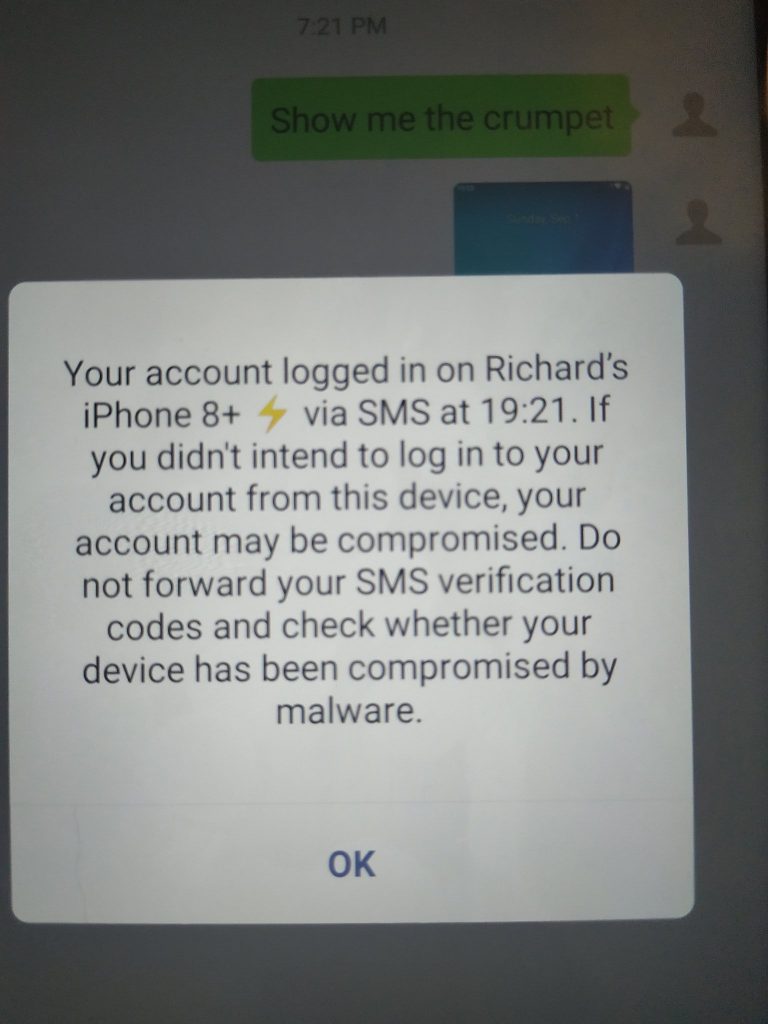
The easiest scientific way to get the bottom of this is Cybergibbons. Like the yard stick of InfoSec he is, I thought it was worth asking if he had a proper WeChat account and if he did, could we steal it. After kindly agreeing, we steal the account. The following screenshot sent from Andrew’s phone perfectly sums up this moment. Crumpet delivered sir.
Ascertaining The Next Steps
Some issues are best dealt with discreetly and this is one of them. At this point I am confident I could steal any WeChat account in the world but other issues could be bolted on to this exploit such as creating accounts for numbers that don’t exist. Creating accounts for numbers that do exist. Could I create an account for Bill Gates if I had his mobile number? Sure.
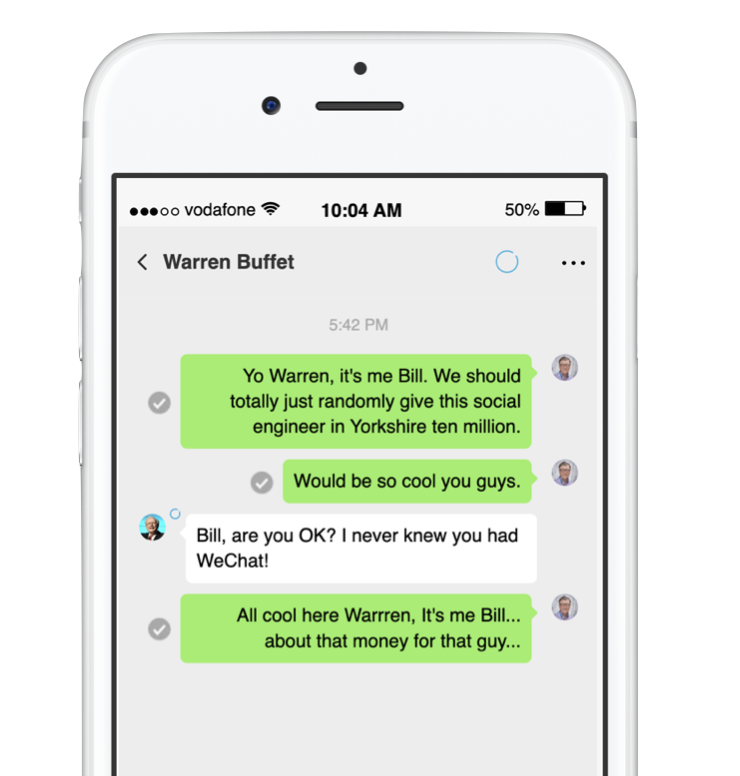
With a couple of hours sat down properly with this issue we found it was possible to:
- Hijack a user’s Session with no interaction from the victim. (Excluding China Mainland Users)
- Create a WeChat account for non existent numbers and genuine un-subscribed users.
- Reduce the barriers to a victim’s payment facilities and obtain the chance to guess the 4 digit card unlock pin.
- Hijack a session with ‘Log On With WeChat’ enabled and use that to pivot to third party services. (Excluding mainland China)
Reporting to Tencent
People don’t talk about it enough but when you report a security issue to the standard UK/European company it is normally hard work. Some of these people just don’t want to listen. Companies have even threatened us with legal action. I have been left disgruntled with HackerOne after finding similar SMS flaws in Twitter.
We now use a fairly standard in-house reporting procedure, but we silently expected every issue under the sun. Tencent is a giant of a company, they are the other side of the world, they speak a different language, they were (at the time) in the middle of an epidemic. This could have been a nightmare…
Wow was I wrong. If you are looking for one of the best examples of how you do a security reporting project, just have a pop over to TSRC and see for yourself.
I reported the issue, as per their bug bounty process and got chucked in triage. I wasn’t speaking to despondent customer service agents in a call centre, they had great technical understanding and the process was so smooth. If you are in to bug bounty schemes please give them a look in. I’m not just saying this because they paid me a fair amount for my time, but because they are true hearted geeks that care with a top platform to handle everything.
To Wrap Up
I mentioned this blog wasn’t about the technical steps needed to exploit this issue at the start and to put some context to that I need to explain the biggest takeaways for me and what I learnt. It’s a blog about trying and going with gut instincts sometimes.
Still amazed that without really trying the issue was quite apparent and obviously displayed. Remember the bit when I tried to convince myself it was unlikely because they have a billion users? Well WeChat do, but the majority of these users are in China and you may of heard they have a rather hands on approach to communications over east.
Put simply, in China you can’t spoof a text message. They seem to have just fixed this issue many years ago… you also can’t share a link in an SMS which again, I won’t go into the politics of such restrictions but that combination sure as hell reduces a lot of fraudulent behaviour.
Because of this fact, a whole nation of developers, security professionals and app builders have just never really factored in SMS authentication risks. This obviously leads to problems when apps, such as WeChat reach a global user base that spans across countries – many of these countries introduce new vectors of attack that might not be seen from that neck of the woods. For me it was a strong reminder to keep going and remember that we all have our minor part to play in securing things. We were able to find many examples of people being suspiciously logged out of their WeChat accounts on forums, so again this adds to shock that we found it even after the likelihood it has been exploited before.
InfoSec is a rather closeted industry and maybe we should be more curious, cross international waters sometimes and look for issues in far corners of the world. It doesn’t have to be 500 people huddled around Zoom poking it just because that service is in focus at the time.


