Followers of the blog will know that I’m not a fan of SMS. It’s spoofable, it’s hackable, it’s from 1981. I can’t even have a meal out in peace without finding SMS weaknesses that take over some random service. So when I hear it will be the very crux of the upcoming track and trace program I decide to see how the latest implementations are to be used.
Not actually seen a real text message yet informing someone of the need to contact track and trace, so I had a look on the official website for more information. It’s all quite clearly laid out, data protection policies, all very transparent but one paragraph got my attention.
What information is collected and why
These people are either sent a text message or email or are called by someone working for NHS Test and Trace Service and asked to confirm or provide their:
full name, date of birth, sex, NHS Number, home postcode and house number, telephone number and email address, COVID-19 symptoms.
https://contact-tracing.phe.gov.uk/help/privacy-notice
At least some of this process will involve sending text messages out to the public and the topic of conversation is going to be their sensitive details. If you ever want my attention, a paragraph about personal data and text messages is how you get it.
Best-laid Plans
So whilst insecure text messages are enabling scams across the world, you may be wondering why they are so ubiquitous. That’s easy – because everyone has SMS! SMS just works. I couldn’t think of a more viable solution to message 60+ million people… you could push millions to Facebook’s WhatsApp messenger but that would never end well. Options are limited, so it’s important not to berate Public Health England for using SMS.
But. There are some protections that could have been done to minimise the risk from social engineering attacks. We’ve already seen an increase of 600% in coronavirus scam emails and reducing the impact from frauds should have been on their agenda somewhere in this project. I don’t think SMShing was factored in that well.
The official website also states that genuine text messages will come from the sender ID of ‘NHS’. Using my preferred SMS spoofing tool, I pinged myself a test NHS message to my phone. Sure enough, seconds later a text message claiming to be from the NHS was delivered.
It’s all very disappointing really, it makes me bang my head on the desk in frustration. The NCSC’s own guidance covers this extensively.
Surely the domains will be better…
The website alludes to the fact users will be asked to log on to a portal to submit information. So my next train of thought was to check what domains people would actually be going to https://contact-tracing.phe.gov.uk/sign_in by the looks of it. We simulate these kind of social engineering frauds every week but the basics of the scam for those that don’t know are blisteringly easy. You go to a domain registrar and see how close you can get to the real domain… we will get on to domains later. So minutes pass and I was the proud owner of phe-gov.uk.

By changing a full-stop for a hyphen, I have changed the whole domain. This was a little cheeky, but I thought best to grab it and use it for security awareness before someone else utilised it for a real scam. If Public Health England want them, just ask us and once validated, we will transfer to safe hands.
What does this scam look like?
This blog post might seem like much ado about nothing, but it’s probably best to show you how this scam could look like if it was conducted by a fraudster:
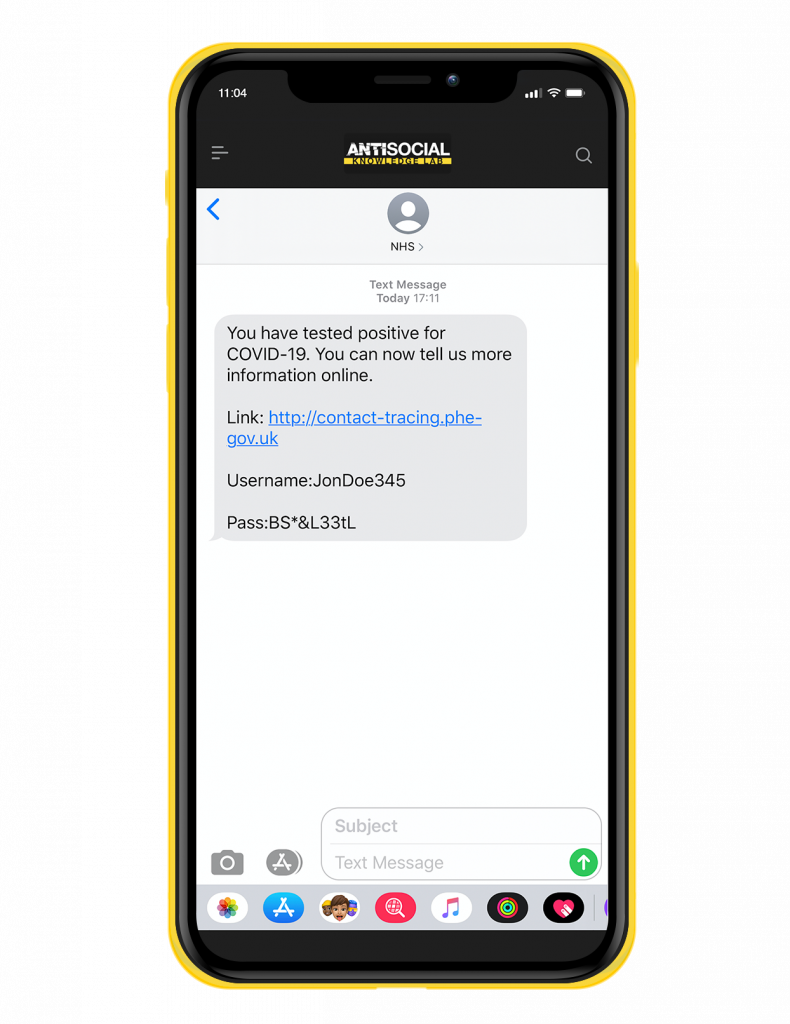
Of course, I’d rig a malicious portal to accept any username and password combination and go a step further. It would be trivial to add a few more fields to a clone of the original form… credit card and CSV for ‘ID validation’ perhaps. Once you are on the wrong domain anything goes, it’s no longer the safety of the genuine website. With a little imagination you could even ask people to connect via TeamViewer to ‘consult with a doctor’ which of course would just be me in a white coat asking for your PIN number…
Learn about domains
It’s sometimes hard at events, showing restraint around CISOs that state “people are the weakest link” and “they must be stupid, what’s not to get”.
The truth is that domains are one slippery slope of knowledge, once you learn to work out and decipher all the parts of a basic domain you get catapulted into a world of homograph copycat domains and bitsquating. You’re found several years later, under a bridge, clutching a blanket and mumbling something about DNS hijacking on a legitimate domain you visited for a recipe.
The populace of the UK just don’t know these little details, yes they can read and know the difference in the domain if they focus, but do they understand the risk? Did they slip up because they panicked and thought for a moment they had a deadly virus?
Ever in the spirit of trying and with no judgement here, lets take a second to learn about domains now. If you click the picture you will get a high resolution version of our domains infographic which would be great to share with your friends and families.
Why is SMShing on the increase?
We have closely followed SMS based scams since our company was founded and sadly many contributing factors seem to be exacerbating text message frauds. One key trend is that email security is getting better and it’s harder for criminals to reach the inboxes and conduct phishing scams. SMS is the perfect solution to this problem as only the bare minimum is being done in this sector to stop fraudsters. Messages land straight in the target’s inbox all the same. Criminals can reach out to thousands of people at once and if you don’t understand about Sender ID spoofing you are an easy target.
We also think it’s because in the hope of the worldwide digital adoption, many online services need customers to have one foot in the past, making use of a universal platform we all have. Yes WhatsApp uses end to end encryption, but they still support SMS signups don’t they. Your online banking portal gave you that card reader for extra security right? but you can still reset and request a password if you have the mobile phone of the account holder. Lost your email password? no worries, just roll right up and we will send you an SMS code. It’s everywhere.
The top five SMShing tips from us
- TRUST NO SMS – You get a text message saying you have a parcel at reception from your colleague, is it a scam? Who knows… probably not… but if that’s a regular old SMS you can’t be sure. Anyone could have sent that message. The Sender ID can be spoofed easily, so next time you get a message from ‘YOUR BANK’ remember not to give it much credibility on that point alone.
- REMOVE IT FROM PROCESSES – We have examined business processes and found SMS to be everywhere. Things like “When you arrive by car at the office, you just send an SMS to the gatehouse and they open the gate.” If you’re designing a new app or a funky new website, can you do it without SMS and future proof it? Do you instruct employees via SMS? Stop it.
- USE THE WEAKNESSES AS ADVANTAGES – So you receive updates from ‘WORK’ and they won’t stop using SMS… well I understand that. But if a fraudster also uses the same sender ID ‘WORK’, their message will appear directly below a legitimate SMS message from your employer. So use that space for security awareness – send out updates to all staff as part of security awareness training. “Everyone, please note, SMS is insecure and scammers could send you messages that appear right here in this message chain. Please speak with IT if you want to know more.” We also perform text message phishing simulations.
- LINKS ARE HONEST HERE – So in an email, people can use a hyperlink to mask a URL. So you see some highlighted text in the email and it says “click here” but actually goes to ‘https://scamsite.com‘. Well in SMShing attacks, scammers can’t do that. So you have the rare advantage that links are honestly displayed. What they do to get around that is what you read about above. They also use link shortening services or compromise legitimate websites to host nefarious payloads.
- RAISE AWARENESS – Education is never wasted and learning about SMS scams is comparatively easy, ten minutes reading this blog could be the difference between falling victim to a scam or being able to identify one. Awareness doesn’t stop there though. SMS is big money and operators don’t want to see text messages go. They are also fully aware that the compensating security controls we have suggested to them, such as blocklisting some sender ID’s are possible.
Want to learn more with us?
73% of employees in the UK do not receive any cybersecurity training. Often these people are the first line of defence when dealing with social engineering attacks. We’ve created a complete security awareness and learning resource platform. It’s training that makes complex issues understandable. Visit Knowledge Lab.