It can be easy to think that phishing attempts are nothing to worry about. After all, you’re never going to click on that email saying you’ve missed your Netflix payment when you cancelled your account back in 2018.
But the reality is, phishing attacks happen. They work, and they’re profitable. If this wasn’t the case, they wouldn’t be so prevalent. According to Verizon’s 2020 Data Breach Investigations Report, 22% of all data breaches last year were a result of phishing alone.
And whilst a criminal having access to your Netflix username and password might not be the end of the world, if you’re targeted in a work setting, the consequences can be devastating.
Five Simple Steps
Spear phishing can be like working as a car salesperson. You spend hours, sometimes days, building up a rapport with a customer, hopeful that they’re going to buy whatever you’re selling. If, at the end of the road they turn you down, it’s time wasted, and you’d better hope the next person says yes.
The same goes for phishing. When a criminal plans a targeted attack against an individual or company, it involves a lot of research, planning, and dedication. For the best chance of success, they need to make you trust them – and there are many ways they can do this.
One of the most popular services we offer is simulated phishing attacks. Our talented developer crafts intricate emails that perfectly mimic their real counterparts. We then decide on a tactic, with the aim of testing your employees’ ability to spot a phishing attempt.
And boy, does it work.
Last year we hit the goldmine – the downloading of an employees’ entire mailbox.
Obviously this is all legitimate and ethical and we were hired to do this, but if we can do it, so can criminals.
There were five simple steps to this attack:
This is how it worked…
The Recon
Our research started with simple OSINT – Open Source INTelligence. This literally means conducting research using open-source, readily available, legally-obtained data. Basically, looking people up on Facebook, LinkedIn, and the rest of the internet.
We’ve all probably done some form of this before, so it’s easy to imagine what this looks like. Compiling a list of social accounts, usernames, groups or interests, and using them to build a picture of who this person is.
In this case, however, all we needed was the name of someone in authority. Someone we knew people would easily trust, especially when it comes to tech problems. And all we needed to do was browse the company’s LinkedIn.
Hello, Ben Hall, IT Manager.
The Spoof
When it comes to choosing an email address, you can either keep it simple, or go all out. If we’re attempting a phish on a company that you would assume to be tech savvy, such as a company that creates software or an insurance company that holds a lot of highly sensitive data, we might go as far as purchasing a domain.
We aim to get as close to the original company name as possible – it might involve simply switching out the letter ‘l’ for a capital ‘i’. If someone were to hover over the sender’s name to check the email address is legit, this would fool them in many cases.
On this particular job, we didn’t think we needed to go that far (and we turned out to be right!). We simply set up a Gmail address using Ben’s name.
Although any emails sent from this account will pop up as being from Ben Hall, all someone would need to do is hover over the name and uncover the email address to raise suspicions. If an email that is supposed to be from your IT manager comes from a Gmail address, needless to say, you should inform said manager immediately!
The Plan
Many phishing attempts aim to create a sense of urgency, ensuring that the victim doesn’t have time to think it through and consider the potential consequences.
In this instance, we went for a simple but convincing route – the IT manager thinks your account may have been compromised.
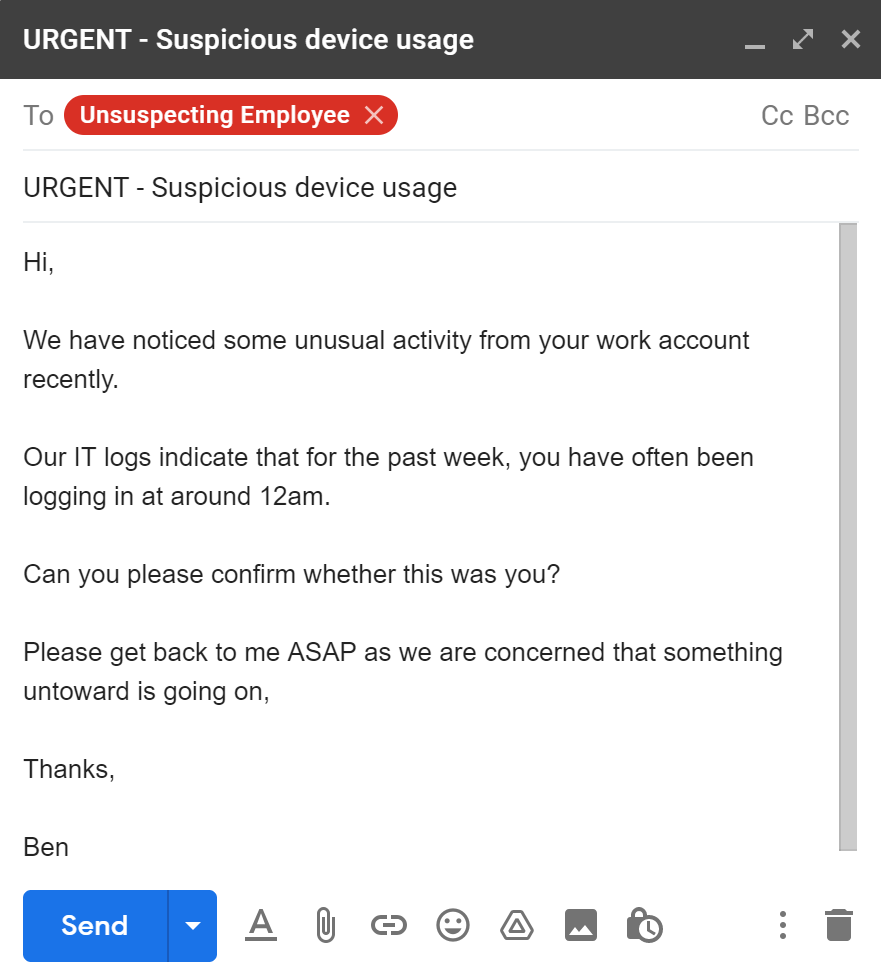
The mark (chosen target) was more than happy to help the IT manager and let him know that unsurprisingly, he hadn’t suddenly developed a taste for midnight working.
The mark genuinely seemed to believe we were the IT manager, so we responded quickly to maintain the sense of urgency.
The Devices
The response we sent was the part of the plan that would either make or break this phishing attempt.
We had informed the mark that he needed to log into his account to verify it was him, and so we helpfully provided him with the link he needed to do so.
A common piece of advice when it comes to avoiding being the victim of a phishing attempt is to never log into a link you receive in an email – always visit the site directly.
But, when it’s your IT manager sending you the link, often this advice will fly out of the window.
We sat back and waited, and sure enough, the mark had clicked the link, not noticed that the login page was a fake one created by us, and logged in. His username and password were captured on the system, but we knew there was one final hurdle.
He had multi-factor authentication (MFA) set up on his account.
This is where most phishing attempts would fail – with a notable exception for modern reverse-proxy phishing tools. Unless they had also managed to steal the mark’s phone, there is no easy way to get the authentication code.
Unless, of course, the mark trusts you and thinks you’re his IT manager…
The next email we sent was short and sweet.
We thanked him for logging in and confirming it was him, informed him that we would be sending over a 6-digit code and asked him to send us this in an email.
We didn’t explain why we needed it, but we had already planned out a few different responses we could come back with in case he questioned us.
But again, he thought we were his IT manager, so the mark did as we said.
A few minutes later, we received an email from him.
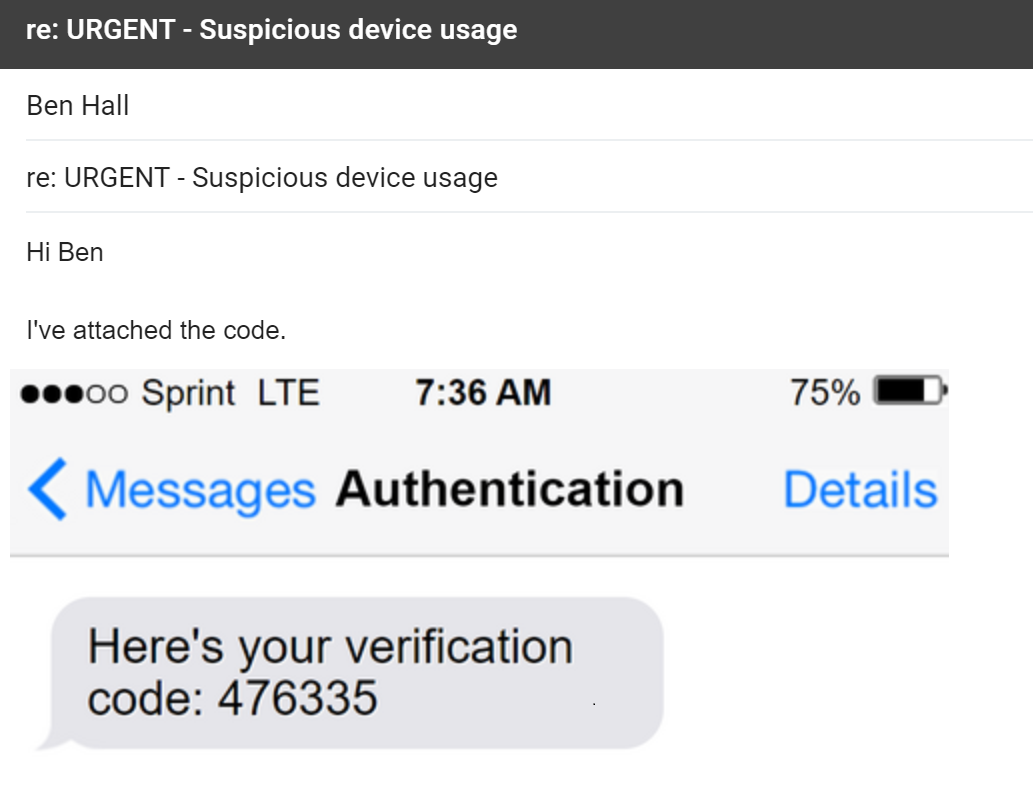
Dramatic reconstruction of the mark composing his response.
He’d taken a screenshot of the verification code and sent the whole thing to us – result!
One final email to the mark put his mind at ease, so that we could be left to our own devices.
We thanked him for sending over the code, and told him we’d look into the issue and fill him in by the end of the day.
The Sync
Now we had everything we needed, it was simply a case of logging in and seeing what we could get our hands on.
If you think you may have been the victim of a phishing attempt and fear you’ve had your credentials compromised, the first thing you need to do is change your password – before the attacker beats you to it.
Our plan wasn’t to lock the mark out of his account, the plan was to get access to as much data as possible.
We did this by syncing the mark’s emails to our device.
Within just 15 minutes we had over 1,000 of his emails saved onto our device – this meant we could peruse them at our own leisure without the fear of him changing his password and kicking us out.
We now had access to everything he had ever sent and received. It was clear that he never deleted emails as there were all kinds of sensitive data, so if this was a real attack, the company would be severely at risk.
The Solution
Prevention is the best cure. Rather than just having faith that you won’t be a victim of this kind of attack, you should take precautions now to lessen the damage if it did happen.
Start by deleting any sensitive emails out of your inbox and sent box once you have finished with them. Save any attachments in your company’s file storage database rather than using your inbox as a point of reference.
And, most importantly of all, never, ever send an authentication code to someone else.
*Names have been changed to protect the identity of the company.


