At the end of last week, news organisations started reporting of a ‘sustained and determined attack’ against the mailboxes of the 650 members of parliament and staff. In the initial release of information it is quite clear the login portal was the target of an automated attempt to log-in and subsequently the log-in portal has been taken offline. Somewhere in the media spectacle the fact that this kind of attack is a very common one has been lost, organisations are likely to see attempts like this weekly and it’s vital businesses learn how it happens. Attackers cobble together this attack from 2 simple stages, OSINT and Exploitation. Whilst this is believed to be a one off attack we can learn to secure any organisation against similar techniques. Let’s have a quick run through of the Parliament attack and see how it compares to the average business!
OSINT
So the target of this attack would be the email login portal of the organisation. This portal is likely to require a username and a password.
We are not going to find the passwords using OSINT, unless there is truth in stories about Russians already having them..
so we will move on to acquiring the MP’s email addresses. If we look at the Government as a business, then the MPs are like the employees. Hackers will hunt for a list of your employees names online, using social media they will search for people that work at the business. In this instance their job has been made a lot easier by the fact you can obtain a list of all these MPs by simply visiting Wikipedia…
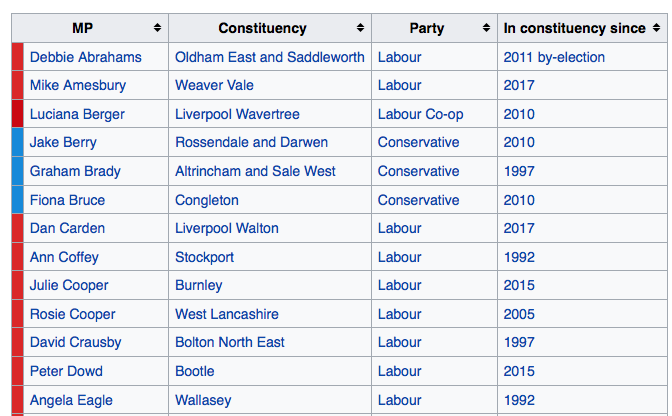
A list 650 British MPs obtained from Wikipedia.
Wherever your staff names are publicly affiliated with your business they will be collated and used in this manner. Hackers will dump these names into a text editor and sharpen up the data – cutting duplicates, making sure that the o’hare’s of this world sit neatly along sides the eaton-smiths.
Next we need to hunt for an email convention. If this is your first rodeo, an email convention is the format an email address is displayed. Be it J.Smith@, John.Smith@ or John@.
To discover this we simply need to find a few addresses online and have an educated guess. With this being public knowledge again, we head over to have a Google, the first link is the directory of MPs. I must say in comparison to a normal business the information available about the houses of parliament is infinitely richer and structured.
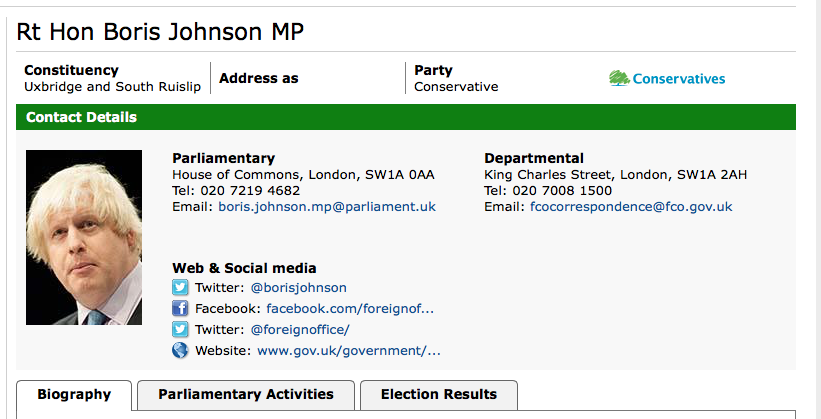
Profiles and contact details of all MPs are obviously public knowledge.
So the email convention is [email protected]. All that leaves is structuring the list of staff names to match this, suffixing each line with ‘@Parliament.uk’ and we have the list of addresses – the heavy lifting has been done!
What happened next might differ for the average business attack, but lets assume the people that had the audacity to do this also knew what they were doing. We still don’t have any passwords for the emails so rather than trying Password1 on this list and blowing the cover of an attack, a further step of analysis would of happened.
Running the list of emails through the other data breaches might of uncovered emails addresses that have had a password leaked… this might add a few guesses at the passwords of the MP’s. It’s unlikely but a better guess than the Password1 we would of had to try if you had nothing. Further recon and attacks might conjoin a this point. Maybe the MPs were victims of phishing credential capture? What if intelligence gave them pets names or names of their families… at this stage this other intel would be used to make detailed lists.
I’m going to omit the next bit of OSINT from this post to help ward off the under 15’s that might be tempted to have a crack, but we will need to uncover the login portal URL or email directory login. It took me about 5 minutes to find. The external logins for your own businesses can usually be found by DNS subdomain enumeration in about the same time.
We now have a list of 650 MPs email address and lets say 30 passwords from the LinkedIn data breach.
Exploitation
So for this we place the previously obtained credentials into programs such as Burp Suite. What Burp Suite is going to do is watch you go to the email login page once and pin point what elements of the site are email address fields and password fields. It will then exchange these for your lists and try hundreds of details per minute. It will time the response and when there is a discrepancy in the timing, it can indicate which password is successful.
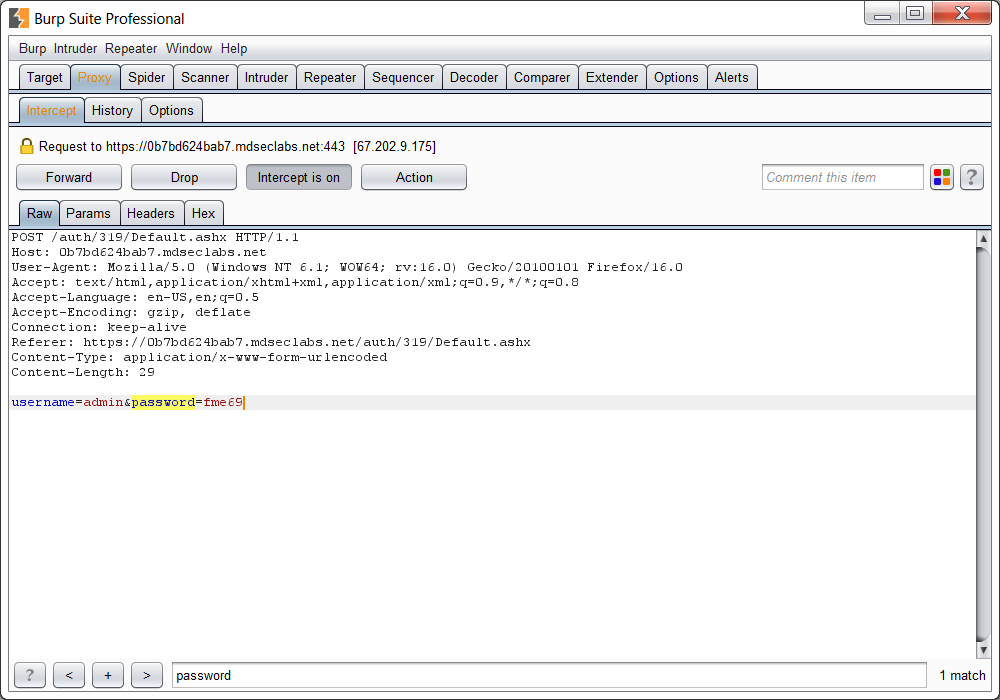
Screenshot of a demo session of BurpSuite.
The Aftermath
Lets be clear, these kind of actions have the hacking hallmarks of rogue bandits. This is a loud, noisy attack, I wouldn’t like to speculate on a country of origin but I can assure you they have the sophistication and tact of Fred Flintstone. Don’t let the media feed the idea that this is the remit of nation states, I mean if you’ve read the blog slowly you could have performed the attack in roughly the same amount of time!
Shortly after this event accounts would of started to get locked out – because these cyber criminals were ram-raiding pirates and didn’t want to run this attack slowly over several days! MPs start to ring up and whinge they can’t get on their emails. An hour later a lot of MPs have rang up and you start to panic. You look at the logs and you discover above mentioned attack all over the logs and panic. The media quickly portray this with added sprinkles on and it is a shame that the interest in this attack isn’t spent on defending against this!
Quick Defence Pointers
- Limit brute force and list attacks by having a incorrect try lockout set to 3/4 attempts.
- Rate limit login attempts. If you have 650 staff you do not need to accept more than 650 attempts every 15 minutes I guarantee it! adjust if you can.
- Have canary files where possible to discover the nosey people that are looking at the PDF file called ‘Passwords’ from 3 years ago.
- If possible tell staff to not associate with the business online unless they have a good attitude to cyber security.
- Install basic network tools that monitor for this and will send a quick email to inform someone they are under a login attack. This can be a really basic setup – It just gives you chance to pull the services down and manage an attack.
- Above all just be aware, long gone are the days of ‘non public email address’. All but the most basic of attacks use these methods!
If you would like assistance in testing for issues like these, make contact today.
 Richard De Vere (@AntiSocial_Eng) is the Principal Consultant for The AntiSocial Engineer, he has an extensive background in penetration testing and social engineering assessments, including ‘red team’ exercises and information gathering assessments for financial institutions and some of the UK’s largest companies.
Richard De Vere (@AntiSocial_Eng) is the Principal Consultant for The AntiSocial Engineer, he has an extensive background in penetration testing and social engineering assessments, including ‘red team’ exercises and information gathering assessments for financial institutions and some of the UK’s largest companies.




















