We had the pleasure of attending the Cybersecurity Leadership Summit 2018 Europe in Berlin and thought it would be a good idea to capture some of the event and hopefully pass on some of the conference for people who did not attend. Kuppingercole hosted the event.
John Tolbert | Kuppingercole
John’s talk focussed on the roots of social engineering, dating back to the great social engineering attacks such as the alleged Trojan horse that breached the walls of Troy. As dates fast forward social engineering attacks take a digital stance, targeting victims with common tactics such as elicitation, pretexting and quid pro quo.
It was nice to see such a broad overview of social engineering attacks. All too often we can fixate on the glossy attacks and forfeit the much needed conversation that focusses on the basics that could serve to protect a lot of people. It wouldn’t be a social engineering talk without a mention of phishing and its dangers and John details the common kinds of phishing techniques – whaling, spear phishing and such.

Richard De Vere | The AntiSocial Engineer
My talk focused on the things an organisation can do to prevent social engineering attacks. To me, the importance for a corporation is more on the learning objectives and educational improvements. This is a transition from my earlier days in social engineering where ‘the chase, the attack’ was everything. Whole years of my life were lost to ego fuelled pen test binges. With experience, I learnt that the importance should be on the simple things a business can do to raise awareness and stay safe. If you are a pen tester – in any guise and you genuinely believe you have magical powers, I’d advise you to take a step back and to re-asses the whole scenario. Are you a skilled master of the arts… or is it just the fact a lot of businesses are insecure in one way or another. What can you do to secure a business – once you’ve shown them your fancy attack simulation.



Zoe Rose
Ethical hacking was the focus for Zoe’s talk, I had the feeling that Zoe’s softly spoken persona did not match the skills and nefarious capability she so obviously conceals. It was refreshing to hear someone that knows the score regarding testing and the clearly defined types of security testing. Social Engineering testing differs from Red Teaming and awareness building and Zoe was all over these important differences. My only small criticism of this highly beneficial talk was downplaying the need for automated testing whilst later highlighting companies should highlight vulnerabilities better. There isn’t many people I meet being antisocial and all that, but I’d enjoy a further conversation with Zoe. She definitely all the right boxes as a tester on the front line of online security.

Panel Session | John Unsworth, John Bryk, Ammi Virk, Markus Krauss
Probably the one panel session I thought was a ‘do not miss’. We often hear of threat intelligence but what does it all mean? the phrase of threat intelligence seems to be purposely misleading. The panel weigh in on ‘Operationalising Threat Intelligence’. In layman terms, let’s get actioning some of the intel and start making secure choices on the back of all this data we have available to us.
Intelligence is information that’s been correctly analysed and utilised. – John Unsworth – Revak
John Bryk’s 9-5 is securing the downstream oil and gas industry n the states, often working with CNI sites. He thinks threat intelligence should lead intelligent decisions. It is hard not to agree with this point as information is one thing but what you do with this information is key. Data alone does not secure anyone – sensible data driven choices do.
There was some really good insights here from people who have dealt with risks for most of their careers. A large takeaway from the talk was pushing organisations to make better use of analysis. Action more! Challenge how you deal with risk. Stop the paralysis through analysis.
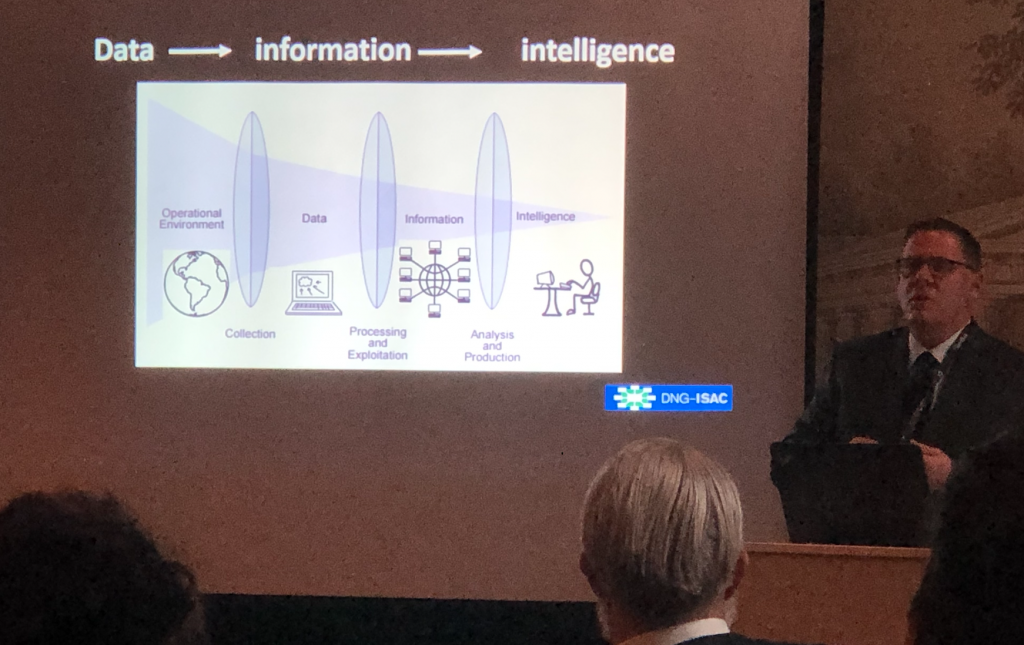
John Bryk | DNG-ISAC
Johns talk took the confusing elements away and simplified the topic of threat intelligence. Making sense of the myriad of data source was somewhat of a focus. He viewed data as irrelevant unless it could be supplied with context. Sharing information between organisations is so important. In the UK we are actually quite advanced at this – platforms like CiSP aren’t perfect but they seem to be ticking a few of these boxes.
Amongst these talks was a real bunch of passionate people, many chosen for their roles in the industry and the whole event came together in a very methodical German manner. It really was a unique conference that focussed on what a company can do!


