It’s been quite a week in the media for VPN providers. Two large companies have had breaches of security in some way or another and the industry dumpster fire has had a fresh poke and a few new logs chucked on. Talk is rife with recommendations and opinions and you know what? We think a lot of them are crap.
So I am sure readers are sat on the edge of their seats wondering why our opinion, probably the 28th one you’ve heard is worth listening to… and for this, I really do need to zoom out a little.
What is a VPN?
For some, a VPN is a critical part of network infrastructure that protects their life, freedoms and secrecy. A journalist in Sudan. An online arms dealer in Brazil. A hacker in France. This is a world where a DNS Leak could mean a door gets kicked in. The VPN is only one part of the story too with the TOR network and compromised servers around the world powering your proxychains setup. For these people, privacy is a lifestyle. They have extensive knowledge of networking and probably have tried Arch Linux more than once.
Now it’s all well and good that exists if that’s your bag… but for most people, it’s a massive turn off and adds to the confusion around VPNs. Good quality Simple VPN advice is rare these days!
Down at the other end of the scale, people look to VPNs to access television channels that aren’t available where they live. You just download an app, select Washington and binge-watch HBO right?
What does a VPN do?
So let’s take the cliché coffee shop scenario. You are sat there with your mocha latte cinnamon-spiced thing and your laptop is sending data through their free WiFi. Their router is then sending that to… well… to be honest, it could be going anywhere! That is what a VPN is going to help with – securely routing your internet traffic to a trusted network or endpoint.
Now at this level, in the room, hackers can also be on the Wifi and try to connect to your laptop. They could try to hack the device directly. A VPN won’t stop this, it is just two machines, IP address vs IP address on the same network mano a mano.
To reiterate, what a VPN does well is protect the network traffic between your laptop and the web-service you’re visiting. Sort of…
What do you mean ‘Sort of’?
If your laptop is sat there in the coffee shop and you are on your banking website and you have a VPN enabled the chances are the connection between your laptop and the VPN is secure. People will not be able to mess with your network traffic in the coffee shop and even the coffee shop’s ISP. But when your traffic gets to the VPN server it’s just chucked out of the moving car and free to go on its way.
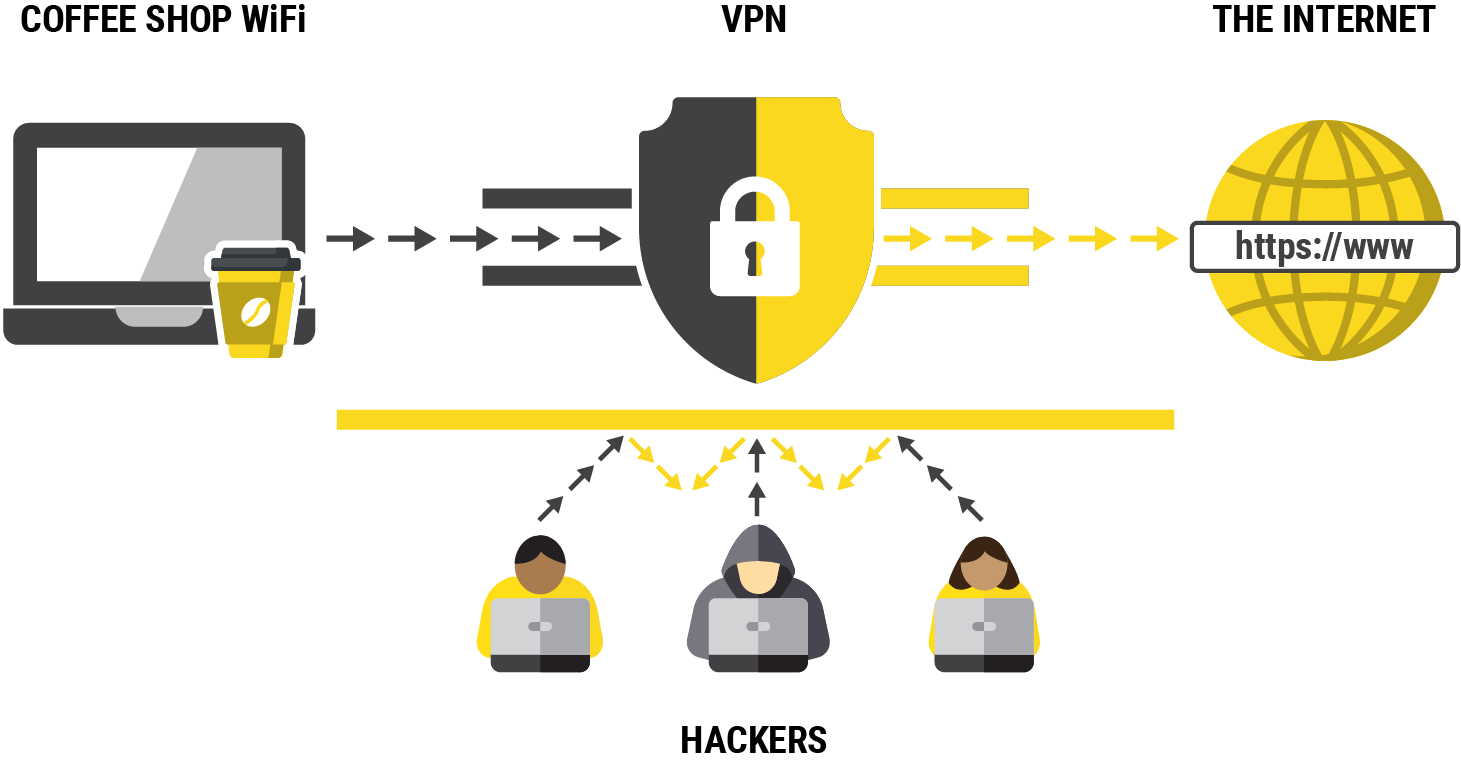
The secure bit of this leg is in the grey colour above, the yellow part is business as usual for the traffic. The traffic comes back from the bank’s web server, gets back in the car and back down the secure tunnel to your laptop.
Obviously over-simplified.
The point I’d like to make is that a VPN is not an end to end secure tunnel between your laptop and every place you decide to type into your browser! your traffic isn’t immune to snooping. In some circumstances the VPN provider could even be a risk and have their part in intercepting network traffic and recording what you do online.
I’m still no better at choosing a VPN provider though…
Choosing a good VPN matters. With all that we have mentioned above, you wouldn’t want all your secrets flying through some dodgy VPN provider – the risk is they would be able to intercept all of your data. But stumbling on to Google to search for a good solution is just going to end up in a marketing frenzy. Or worse – blatant lies.
That is the sad reality of marketing and InfoSec products, their whole business revenue is derived from selling you the un-hackable dream, whilst also being educated enough to know that a VPN isn’t going to stop your password from being phished or prevent you from many other types of online crime… just about the only thing a good VPN will do is protect one small bit of the picture. It is merely garnish. But “Come and buy our thing that takes you from 45% secure to 49.5% secure” is hardly going to get Mr Salesman their bonus this month is it.
Our advice is choose to back yourself, invest in you. Build your own VPN on a server you control.
Why spend hundreds of pounds securing yourself and the business when you can build a service that has your interests at heart and costs £5 a month…
Oh yeah, let’s alienate people with stupid ideas.
In whatever conversation there is online about VPNs, you will inevitably meet the person who declares that renting a server in Iran and coding your own VPN software is the only way to keep things secure:
Just pipe traffic to a secure bulletproof server in Iran and then use FIPS and a 90,000 bit RSA key to tunnel layer two through TOR then back out into WhoNix. Oh and don’t forget your FIDO keys and magic spell. Simples.
Every nerd ever.
Then the predictable counter-argument…
How is anyone going to make use of VPN services if it’s not simple for the average user?
Every person who has actually had to install a VPN on a relatives device before.
The irony is both of these contrasting arguments come the closest to solving the issue for the majority of small businesses, shops, executives and more. The correct answer is actually in the middle of these statements somewhere.
The solution has to be secure and built with security in mind, normally in an ecosystem you control. But it has to be easy enough that I can text a file to a mate and it just works on their new overpriced iPhone.
Trusting three people with a secret.
We all know the expression, you can trust three people with a secret if two are dead. Well, it works quite well here. We can trust our network traffic more when there aren’t other parties involved. In a way, killing the VPN provider entirely frees you up from scenarios out of your control, such as:
- The VPN provider has been compromised.
- The VPN provider is monetising your traffic.
- The VPN is lying about retaining logs.
- The VPN provider is working with the police.
- The VPN provider is just a server, worse than the one you could build.
Now i’d like to think that our readers are aware enough to realise ANY server we create will have a certain risk, but the risk is ours to manage. We control our destiny and our own web traffic.
Above all, don’t underestimate the security benefits of just standing away from a busy crowd of people.
Building your own VPN server
This used to be a hard task, even with guides but recently easy to use programs can help you set this up with minimal experience. In fact if you have £5 and 30 minutes spare you too can become a VPN provider for your own small business or family.
Many setup guides exist that will help you set up a VPN, but I’d like to recommend inexperienced users start with something like PiVPN – yes it works fine on a standalone server/VPS.
- Create a standard 20.04 Ubuntu Droplet. Following the DigitalOcean guide: https://www.digitalocean.com/docs/droplets/how-to/create/ (other VPS providers work DO is the easiest)
- Head to PiVPN.io and read about the project, it’s just a setup script for OpenVPN… rather than struggling you just run “curl -L https://install.pivpn.io | bash” and installation starts.
- Configure a free DO Firewall to limit all access to the droplet other than the port the service is running on.
- Use the PiVPN script to create new users and you can also revoke them using simple commands.
To Conclude
Like everything else on the internet – you are responsible for what you do! Results may vary and choosing a VPN really does come down to your own attack vectors. Hell, you might be better off just ignoring all of this post and connecting your laptop to your phone instead of the free WiFi next time you are out the office, which would eliminate most of the concerns anyway… but if you desire to follow industry best practice and avoid a chance encounter with a hacker – then a VPN could be really useful. Building ‘one’ and by that I mean configuring a server, is relatively easy and can be helpful to a small business.
Just be sure to dodge the snake-oil sales nonsense no matter what you decide to do.


